Security Approach
These notes on security is included here to help users consider how the different aspects of security could be considered with respect to an RLN implementation.
Information Security
Key to any successful implementation of the RLN will be the adherence of organisations to fundamental information security maxims. Those standards can be examined via standards frameworks such as ISO 27001.
The basic goal of ISO 27001 and similar frameworks is to protect three aspects of information:
Confidentiality : only the authorized persons have the right to access information.
Integrity : only the authorized persons can change the information.
Availability : the information must be accessible to authorized persons whenever it is needed.
Identify which risks exist for the information
- Define controls (safeguards) and other mitigation methods to meet the identified expectations and handle risks
- Set clear objectives on what needs to be achieved with information security
- Implement all the controls and other risk treatment methods
- Continuously measure if the implemented controls perform as expected
- Make continuous improvement to make the whole ecosystem work better
This set of rules can be written down in the form of policies, procedures, and other types of documents. ISO 27001 and other equivalent frameworks define which documents are required, i.e., which must exist at a minimum.
Development Security
Secure development practices are a key part of maintaining information security. OWASP (Open Web Application Security Project) is one of the leading organisations in promoting secure coding and development practices. They describe the objective of secure coding practices as follows;
“It is helpful to understand what is meant by risk, in order to protect the business from unacceptable risks associated with its reliance on software. Risk is a combination of factors that threaten the success of the business. This can be described conceptually as follows: a threat agent interacts with a system , which may have a vulnerability that can be exploited in order to cause an impact. While this may seem like an abstract concept, think of it this way: a car burglar (threat agent) goes through a parking lot checking cars (the system) for unlocked doors (the vulnerability) and when they find one, they open the door (the exploit) and take whatever is inside (the impact). All of these factors play a role in secure software development.”
Software security flaws can be introduced at any stage of the software development lifecycle, including:
- Not identifying security requirements up front
- Creating conceptual designs that have logic errors
- Using poor coding practices that introduce technical vulnerabilities
- Deploying the software improperly
- Introducing flaws during maintenance or updating
Infrastructure Security
Infrastructure security is the set of practices and design principles that secure the operation of an application across a network of services. For the trial we have utilised cloud environments however these principals equally extend to physical infrastructure environments.
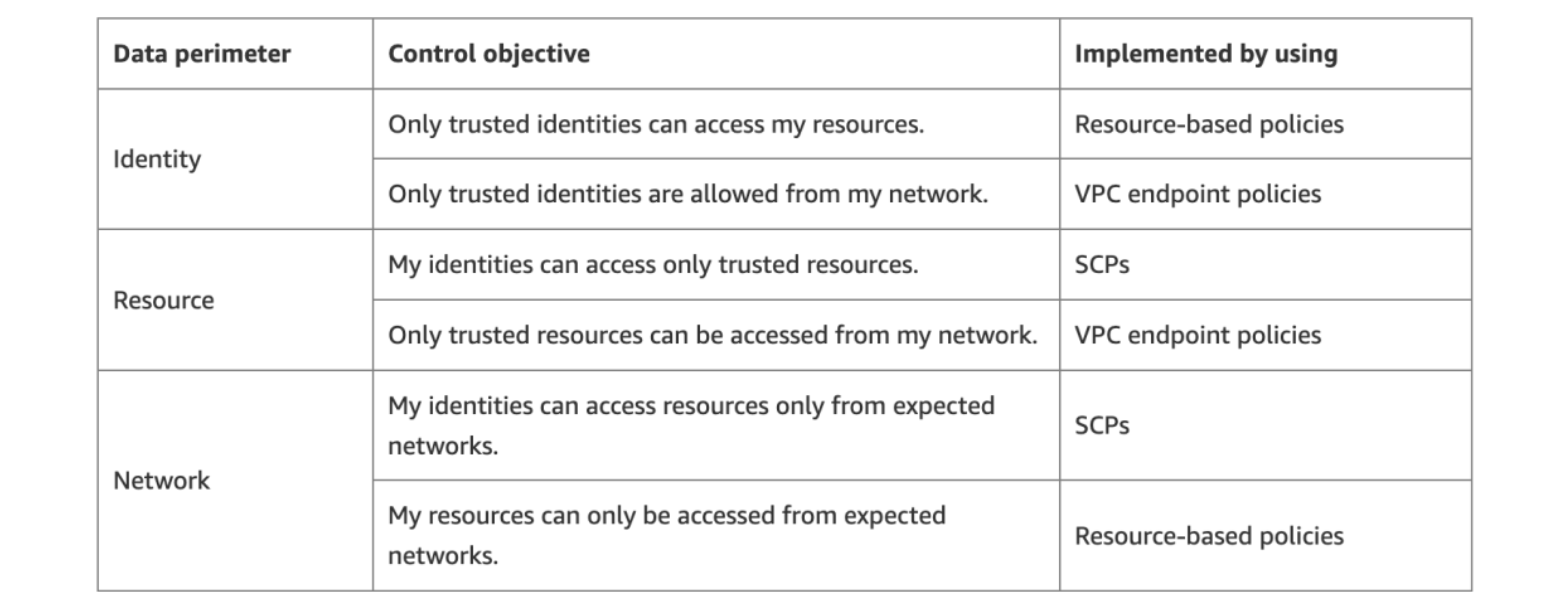
The term ‘data perimeter’ is often referred to within Infrastructure Security and is key to any production deployment of LedgerSwarm. The 'data perimeter' incorporates a set of preventive guardrails that help ensure that only trusted identities are accessing trusted resources from expected networks.